Onboarding: Hacked by my employer?!
Anatomy of a phishing hack during new employee onboarding for a job I didn't know was fake
While the soul sucking wagie existence was oft thought to be the worst part of applying for a job, now job applications or joining a new company can be a vector for getting hacked, and if you have crypto, losing your coins.
This happened to me recently.
Thankfully, I took the DeFi Academy course last year which in combination with reading DeFi Education newsletter, has given me sufficient skepticism to prevent this most recent attempted hacking.
I also took a security course as part of my computer science degree which covered basic exploits and debugging techniques which helped in slowly confirming my suspicions in this situation.
This isn't a sign of pride though, but continued humility that all it takes is one mistake, one moment rushing and not thinking, and my life could look very different.
This post will be a post-mortem for a near SEV and a case study.
I've tried to include my train of thought at the time so you can see how you can get better at discerning what may be a malicious interaction.
Be careful out there, anon.
WARNING
Do not copy code or anything below, unless you are a competent security engineer who wants to debug this further.
DO NOT run any of the below in terminal, unless you know what you’re doing.
This is the last and final warning, do not get yourself hacked out of curiosity.
First off, a special thank you to the readers who pay to make this newsletter possible.Your support lets me continue to share tactics to grow your tech career and in-depth reporting on Canada’s economy, politics, and national trajectory.
If today’s post resonates, please share it with others so more can join the newsletter.
Are you looking for 1:1 coaching on anything from your tech career to Canadian real estate?
DM me on Substack or X (formerly Twitter) with your proposed topic, I’ll let you know if I can help. Skip the mid-IQ takes on Reddit, pay $100 for 25 minutes of guidance you can trust.
Ready to work through the paid subscriber tech career tactics archive? Start here and report back your wins. It’s a growing club of winners, and we’re waiting for you to join.
– Fullstack
A Job Offer
I received a DM last week on X (formerly Twitter) from an account I'll call Kevin. The account had been created in 2013, and seemed to be similar to other anonymous crypto accounts I had seen around.
It was supposedly a recruiter in the crypto space, they saw I followed some crypto accounts and wondered if I'd be interested in a few part-time positions.
I hadn't gotten a DM like this before so I figured I'd engage and see what the offers were.
I was in the middle of reading the BowTied Bull oft-recommended book, the Sovereign Individual, so the idea of getting a job even for a short while fully anonymous and being paid in crypto peaked my interest. The future was here.


Too good to be true...
There were 3 roles ranging from $800 - $1300 USD/week for community moderator, community moderator supervisor, and customer support.
The offers weren't going to be life changing money but would have certainly supplemented my monthly investing cash flows.
There seemed to be sufficient detail that this maybe was a legit offer. I've worked for startups that had worse job descriptions.
I even was starting to think of how I could gradually automate the job using AI tools.
I did find it odd that Kevin wasn't followed or following anyone I did or knew on X.
I also thought it strange that despite recruiting for the Wormhole Foundation, he didn't follow them. But, I chalked that up to him maybe being an independent recruiter for many companies.
I gave some fake information and send back the initial form, just in case it was a scam, and was approved for the position.


Onboarding from hell
Kevin quickly replied saying I looked like a good fit and immediately tried to get me setup with their "team chat" and sent me a link to register.
I always check the X URL preview and saw something strange.
Despite him saying that the team worked on Kakao Talk, the url wasn't kakao.com but kakao.cn.com. A bit strange?
I knew Kakao was a Korean company, and figured it didn't have operations in China, so this was a bit odd.
This should have been my first clue, I later checked with Grok and sure enough it had a conclusive answer which should have eliminated all doubts that this was an exploit in progress.
I decided I would now assume this is a hacker and wouldn't open the link on any personal device.


I started to ask some follow up questions, to sniff out further if this somehow was legitimate.
First, he said the link expired in 6 hours. I waited a day and asked for a new link, and he pushed me to use the original link and now said that it didn't expire.
Kevin then sent long detailed instructions of how the app must first be installed on my desktop and then on my phone. Any follow up questions, he would just push me back to the long instructions.
While waiting for his replies, I setup a local VM to sandbox working with the URL to see what type of exploit it was.
Upon reflection, even using a VM was too risky since it was connected to my main network, and on my primary computer. Escaping a VM is very hard but not impossible for good exploits.
A better approach might have been an old laptop and only opening the URL on a public wifi where even if it did take control of the machine and start attacking others on the network, at least it wasn't my home devices.
Further still, I could have setup a network sniffer app in the VM to better capture any malware making suspicious out bound network calls.


Playing in the sandbox
Once I had a block of time when I could focus uninterrupted, I manually typed the URL in the VM (to avoid accidentally clicking it on my main machine), and started my investigation.
The website opened and looked believable.
Exploit URL (DO NOT CLICK): https://kakao.cn.com/?join=1111-2222.
I changed the join code to avoid potential issues for readers or myself but can provide it to interested security researchers. Reach out on X/Twitter DMs.
Asian characters, FAQ linking to the official kakao.com FAQs, and a simple Download button. It didn’t immediately look too suspicious.
But, before clicking download, I searched in a new tab "Kakao Talk download" to see if this site even ranked and came up.
Sure enough, it didn't.
And every website with an authoritative answer all linked to the Mac App Store. There seemed to be no way to download the .dmg directly in any of the search results I checked.
I still wasn't fully convinced that it was a hack so I installed Kakao Talk from the Mac App Store and tried to follow Kevin's instructions, but sure enough they didn't make any sense or work with the official version of the app.
I asked some more follow up questions and he redirected to follow the link he provided and long instructions.
Want to start 2025 off right and fire your dev team?
Want software engineers who can ship quality & fast?
You need Deca Labs. I’ve partnered with them to offer 10x software engineering talent – including my own – that you won’t find outside of big tech companies.
I still have room in Q1 for another project. Make it yours and your business will never be blocked on your dev team again.
Reach out on X/Twitter DMs or through the website.
Exploit by fake chat app
I hit the download button on the malicious website.
It downloaded a .dmg file, the standard disk image format used by Mac apps offered outside the Mac App Store.
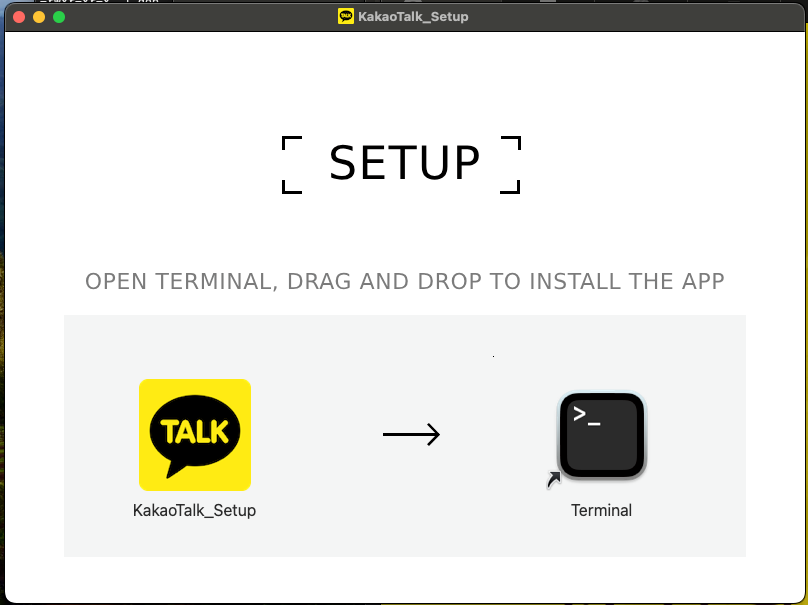
I opened up the mounted volume and it showed a familiar screen. Except for one thing...
While most legitimate application have a similar cute drag and drop install view, the drop target is always an alias to the /Applications folder, not Terminal.
Now, I was fully convinced that this was an exploit. There was no way one of the biggest technology companies on the planet was having their users install an app by command line.
Time to leverage my college security class skills.
Investigating the exploit script
In the volume install window, I hit cmd + 2 which switches Finder to list view.
Notably, the KakaoTalk_Setup file wasn't an application file type at all, but a document. And likely, a shell script of some kind that would run in Terminal if I had dragged it.
I carefully opened it in TextEdit.
Now, this looked familiar from college.
A classic obfuscation technique of encoding the app code as base64 was used. There was no way to tell what the code was going to do, but on the last line the long base64 string was decoded and then executed in a new bash shell.
I opened up a browser and searched for base64 decoder. Then, I carefully copy-pasted the base64 string into the decoder site and could confirm my suspicions. I saved that in a new text file to reference.
The decoded setup code seemed to do all the setup work for a secondary main exploit program. The setup copied it from the volume to the /tmp/ directory, definitely not what you'd expect from a legitimate setup program that should be installing into /Applications/, and then added +x executable permissions so it could be run.
When I went back to Finder, there weren't any other files for the secondary program. I double checked the decoded setup code and noticed that there should be a hidden file .KakaoTalk_Setup which is the main exploit executable.
I hit cmd+shift+. to show hidden files and sure enough it was there.
I carefully opened the 235kb .KakaoTalk_Setup Unix Executable File in Text Edit. One extra click could have opened it in Terminal instead since it was a compiled Unix executable file.



The file contents as expected were compiled bytes, so not human readable, difficult to decipher, and the file was quite long.
This is where I gave up my investigation, thoroughly convinced that this could have been a major hack if I had blindly followed the instructions as given to me by Kevin.
Stay safe out there
Learn from my near miss, invest in your education, remain skeptical, don't fall for increasingly sophisticated hacking attempts, keep your keys, keep your coins.
I fully endorse and recommend both the DeFi Academy course and the DeFi Education newsletter if you want to increase your skills in crypto, security, and investing. They may not know it, but they have saved my ass multiple times this year. Consider both before you get hacked. They are well worth the investment. (Neither are affiliate links, the resources are just that good).
This experience gave me another big lesson and motivation, to keep building out my wifi-money so I never need to interview for a job (real or fake) ever again.
Start here if you want that too.
In other news…